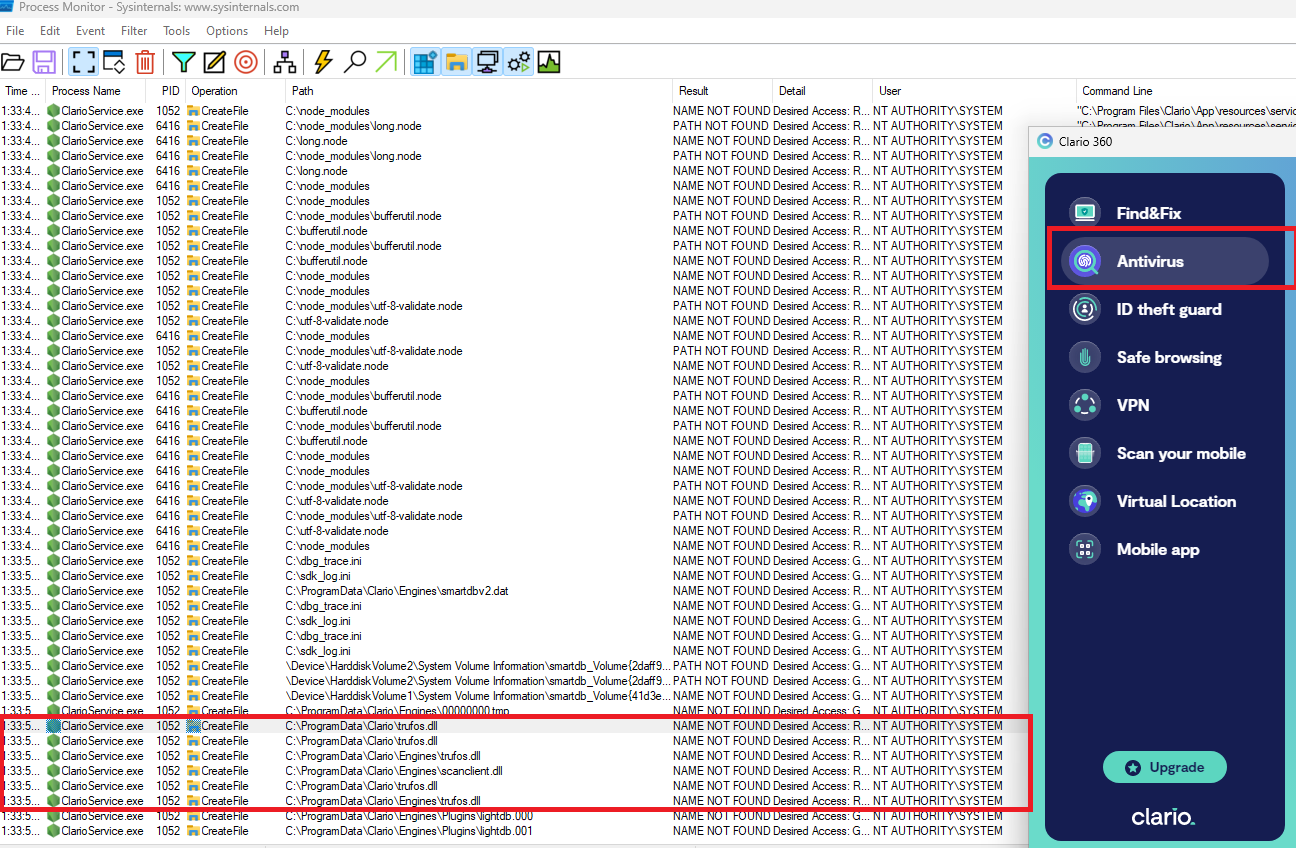
Clario through 2024-04-11 for Windows Desktop has weak permissions for %PROGRAMDATA%\Clario and tries to load DLLs from there as SYSTEM.
Clario for Windows desktop application attempts to load non existent DLLs libraries from C:\ProgramData\Clario\ and C:\ProgramData\Clario\Engines\ when a user performs an Antivirus scan. The DLL files do not exist and this process is invoked with SYSTEM privileges even if a non admin performs it. By default, on windows systems, any authenticated users can create files/Folders under the c:\ProgramData\Clario path. A user with low privileges can create the DLL files under C:\ProgramData\Clario\ and C:\ProgramData\Clario\Engines\ to execute arbitrary code of their choice resulting in elevation of Privileges to the SYSTEM rights.
Clario versions through 2024-04-11
Insecure Folders: C:\ProgramData\Clario\ & C:\ProgramData\Clario\Engines\
Service: ClarioService.exe
Alaa Kachouh